BY DR SOHA MAAD
Introduction
This article overviews cybersecurity threats, challenges and solutions in digital banking with focus on cybersecurity challenges from the COVID-19 pandemic, in particular in open banking. Following this overview, the article sheds light on Windows 11 cybersecurity with reference to Microsoft book and guide “Powerful security from chip to cloud”. The article then addresses the urging question of whether Windows 11 can meet banks and financial institutions cybersecurity requirements with reference to constructive and deep discussions raised during the Union of Arab Banks First Arab Banking Forum for Cybersecurity held on 7-9th October 2021 in Sharm el Sheikh, Egypt. The article concludes with recommendation for sound cybersecurity programs and strategies for banks and financial institutions.
Cybersecurity in Digital Banking
The award winning Enterslice consultancy company identified various threats, challenges, and solutions in digital banking. These are overviewed below.
With increased digitization, cybersecurity threats are growing tremendously. As the world is being increasingly connected digitally, cybersecurity is becoming a major concern in digital banking.
What is cybersecurity?
Cybersecurity is the practice of protecting electronic systems and data from malicious attacks. It is also called Information technology security or electronic information security. Cybersecurity involves technologies and practices designed to protect networks and devices from attack and damage from any unauthorized access.
The primary purpose of Cybersecurity in digital banking is to protect the customer’s assets. As people go cashless, more and more activities or transactions are done online. People use their digital money like credit cards and debit cards for transactions. These transactions have to be protected from cybercrimes.
Cybercrimes in digital banking does not only affect the customer, but it also affects the banks data. Banks may need to spend a considerable amount of money to recover data or information attacked by cybercriminals.
A strong cybersecurity is a must for banks as data breaches may make it tough to trust financial institutions. It may cause severe problems for banks. Cybersecurity in digital banking ensures that sensitive data is safe and secure.
If data is not protected, any data breach may cause substantial financial loss to banks and customers. Without a robust cybersecurity measure in place, sensitive data may be at risk.
Cybersecurity threats
The biggest cybersecurity threats to banks are:
- Unencrypted data: One of the common threats faced by banks is when the data is left unencrypted, and hackers or cybercriminals use the data right away, thereby creating severe issues for the financial institution. All data that is stored on computers in financial institutions or online must be fully encrypted. This will ensure that even if data is stolen, cybercriminals may not be able to use them.
- Malware: End to end-user devices like computers and mobile devices are mostly used for conducting digital transactions and must be secured. Malware pose a serious risk to banks whenever they connect with the network. Sensitive data passes through the network, and if the user device has malware installed in it without any security that malware can pose a serious threat to the bank’s network.
- Third-party services: Many banks and financial institutions use third-party services from other vendors to serve their customers better. However, if these vendors do not have tight cybersecurity measures, then the bank may face security problems from the third-party services.
- Spoofing: This is one of the newest forms of cyber threats faced by banks. The cybercriminals will impersonate a banking website’s URL with a website that is similar to the original one and functions the same way and when the user enters his or her login credentials that login credentials are stolen by these criminals and used later. This cyber threat has gone to the next level where new spoofing techniques have been employed by cybercriminals. Cybercriminals use a similar URL and target users who visit the correct URL.
- Phishing: Phishing is the attempt to get sensitive information such as credit card details for malicious activities by disguising as a trustworthy entity in an electronic communication. Online banking phishing scams have evolved continuously.
Cases of Cybersecurity Attacks in Digital banking
According to a global economic crime survey, cybercrime has increased tremendously and is the most reported economic crime. With the world going digital, cybercriminals have also found new ways to attack and breach data. Worldwide, banks are facing attacks from organized criminals and hackers. An example is a recent case with Canara Bank where a hacker attacked and defaced the bank’s site by inserting a malicious page and tried blocking some of the bank’s e-payments. Factors that raise a serious challenge to cybersecurity in digital banking are:
- Lack of awareness: cybersecurity awareness among people has been quite low, and not many firms invest in training and improving the overall cybersecurity awareness.
- Inadequate budgets and lack of management: cybersecurity is accorded low priority and most of the time neglected in the budgets. Top management focus remains low on cybersecurity, and support for cybersecurity projects is given low priority. This may be because top management underestimate the impact of cybersecurity threats.
- Weak identity and access management: Identity and access management has been the fundamental element of cybersecurity. It may require only one hacked credential to enter into an enterprise network.
- Rise of Ransomware: The recent events of malware attacks bring our focus to rising menace of ransomware. Cybercriminals are starting to use methods that avoid them to be detected by endpoint protection code that focuses on executable files.
- Mobile devices and Apps: Most of the banking institutions have adopted mobile phones as a medium to conduct business. As the base increases each day, it also becomes the ideal choice for exploiters. Mobile phones have become an attractive target for hackers as we see a rise in mobile phone transactions.
- Social Media: Adoption of social media has led hackers to exploit even more. Less aware customers put out their data for anyone to see which is exploited by the attackers.
Cybersecurity solutions
Solutions to curb cybersecurity threats in digital banking include:
- Integrated Security: Banks invest time, money, and effort in employing the best technology which may be sometimes difficult to manage together. Moving towards integrated security where all components work and communicate together is more beneficial.
- Machine Learning and big data analytics: Analytics is an essential element in leveraging cyber resilience. A new generation of security analytics has come out which can store and assess a huge number of security data in real-time.
- Raising Management awareness of the importance of security: Awareness of the risk of security threats and its impact must be raised and well understood and addressed by top management.
- Investment in next-generation endpoint protection: Banks and institutions must invest in technologies that can recognize and eliminate cybersecurity attacks.
- Protecting information: Data is stored in different devices and in the cloud, so every system that holds the sensitive data must be protected with security.
- Raising consumer awareness: Consumers must be made aware of the importance of not disclosing their banking credentials to anyone.
- Using anti-virus and anti-malware applications: A firewall may increase protection, but will not stop attack unless updated anti-virus and anti-malware applications are used.
OPEN BANKING CYBERSECURITY IN FACE OF Covid-19 pandemic
In the wake of sudden and massive remote working environment accelerated by the Covid-19 pandemic, cybersecurity has been placed among the top concerns of banking executives. According to head of KPMG’s Cybersecurity practice in Saudi Arabia, the cybersecurity landscape is rapidly evolving, and there are several key developments that are shaping cyber in the banking sector. In line with the acceleration of digitalization, the prevalence of cybercrime has increased during the Covid-19 pandemic. For banks, the threat is pronounced and growing.
Though better prepared than most sectors, the banking sector still lags behind the cyber threats landscape. Hackers will find opportunities to exploit flaws in the way banks currently fund, manage, enable, organize and implement their information protection capabilities.
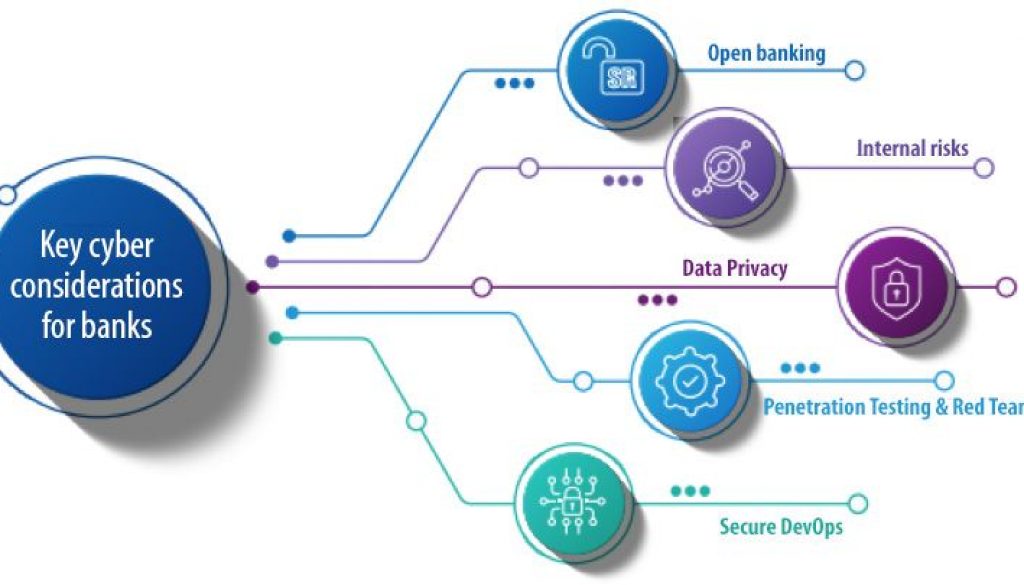
Open banking is a practice that provides third-party financial service providers open access to consumer banking, transaction, and other financial data from banks and non-bank financial institutions using application programming interfaces (APIs). It also allows for greater financial transparency for customers and uses open source technology to build the cybersecurity ecosystem. At each level, cybersecurity measures and policies will determine the success of open banking.
As open banking initiatives are undertaken, the importance of security is rising. All third-party providers have to comply with regulators and bank data protection rules, which should be focused on customer privacy protection. The provider must inform the bank and the customer what data it intends to use and how it will use it, as well as how long it will remain within their system.
WINDOWS 11 CYBERSECURITY
Microsoft developed a short guide and a book on Windows 11 security entitled: “Powerful security from chip to cloud”. Below we overview Windows 11 security with reference to the Microsoft guide and book.
According to Microsoft guide and book, Windows 11 is built with Zero Trust principles at the core to safeguard data and access anywhere, keeping users protected and productive.
The acceleration of digital transformation and the expansion of both remote and hybrid workplaces brings new opportunities to organizations, communities, and individuals. Work styles are transformed. Employees need simple, intuitive user experiences to collaborate and stay productive. But the expansion of access and ability to work anywhere has also introduced new threats and risks. The move to hybrid work leaves organizations more vulnerable to security threats.
Windows 11 is built with Zero Trust principles for the new era of hybrid work. Zero Trust is a security model based on the premise that no user or device anywhere can have access until safety and integrity is proven. Windows 11 raises the security baselines with new requirements built into both hardware and software for advanced protection from chip to cloud. With Windows 11, users can enable hybrid productivity and new experiences without compromising security.
Most security decision makers see that software alone is not enough protection from emerging threats. In Windows 11, hardware and software work together for protection from the CPU all the way to the cloud.
In Windows 11, the Zero Trust principles are threefold. First, verify explicitly. That means always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies. The second uses least-privileged access, which limits user access with just-in-time and just-enough-access, risk-based adaptive polices, and data protection to help secure both data and productivity. And lastly, assume breach. Assume breach operates in a manner that minimizes blast radius and segments access. Verify end-to-end encryption and use analytics to gain visibility to improve threat detection and defences.
For Windows 11, the Zero Trust principle of verify explicitly applies to the risks introduced by both devices and users. Windows 11 provides chip-to-cloud security, giving IT administrators the attestation and measurements to determine whether a device meets requirements and can be trusted. Windows 11 works out of the box with Microsoft Intune and Azure Active Directory, so access decisions and enforcement are seamless. IT Administrators can easily customize Windows 11 to meet specific user and policy requirements for access, privacy, compliance, and more.
Individual users also benefit from powerful safeguards including new standards for hardware based security and passwordless protection. All users can replace potentially risky passwords by providing secure proof of identity with the Microsoft Authenticator app, signing in with face or fingerprint, a security key, or a verification code sent to a phone or email.
Windows 11 security priorities are:
- Security by default: Building on the innovations of Windows 10, Microsoft worked with manufacturers and silicon partners to provide additional hardware security capabilities to meet the evolving threat landscape and enable more hybrid work and learning. The new set of hardware security requirements that comes with Windows 11 is designed to build a foundation that is even stronger and more resilient to attacks.
- Enhanced hardware and operating system security: With hardware-based isolation security that begins at the chip, Windows 11 stores sensitive data behind additional security barriers, separated from the operating system. As a result, information including encryption keys and user credentials are protected from unauthorized access and tampering. In Windows 11, hardware and software work together to protect the operating system, with virtualization-based security (VBS) and Secure Boot built-in and enabled by default on new CPUs. Even if cybercriminals get in, they can not get far. VBS uses hardware virtualization features to create and isolate a secure region of memory from the operating system. This isolated environment hosts multiple security solutions, greatly increasing protection from vulnerabilities in the operating system, and preventing the use of malicious exploits. In combination with device health attestation with cloud services Windows 11 is zero trust ready.
- Robust application security and privacy controls: To help keep personal and business information protected and private, Windows 11 has multiple layers of application security to safeguard critical data and code integrity. Application isolation and controls, code integrity, privacy controls, and least-privilege principles enable developers to build-in security and privacy from the ground up. This integrated security protects against breaches and malware, helps keep data private, and gives IT administrators the controls they need. In Windows 11, Microsoft Defender Application Guard uses Hyper-V virtualization technology to isolate untrusted websites and Microsoft Office files in containers, separate from and unable to access the host operating system and enterprise data. To protect privacy, Windows 11 also provide more controls over which apps and features can collect and use data such as device location or access resources like camera and microphone.
- Secured identities: Passwords are inconvenient to use and prime targets for cybercriminals and they have been an important part of digital security for years. That changes with the passwordless protection available with Windows 11. After a secure authorization process, credentials are protected behind layers of hardware and software security, giving users secure, passwordless access to their apps and cloud services. Individual users can remove the password from their Microsoft account and use the Microsoft Authenticator app, Windows Hello, a security key, a smart card, or a verification code sent to their phone or email. IT administrators and consumers can set up Windows 11 devices as passwordless out-of-the-box, taking advantage of technologies such as Windows Hello in alignment with Fast Identity Online (FIDO) standards. Windows 11 protects credentials with chip-level hardware security including TPM 2.0 combined with VBS and Microsoft Credential Guard.
- Connecting to cloud services: Windows 11 security extends zero-trust all the way to the cloud, enabling policies, controls, procedures, and technologies that work together to protect your devices, data, applications, and identities from anywhere. Microsoft offers comprehensive cloud services for identity, storage and access management in addition to the tools to attest that any Windows device connecting to the network is trustworthy. Compliance and conditional access is enforced with a modern device management (MDM) service such as Microsoft Intune that works with Azure Active Directory to control access to applications and data through the cloud.
Windows 11 for BANKs and businesses
The big change for bank and businesses in Windows 11 is commerce and security.
Microsoft is expanding in five key areas of interest to banks and businesses:
- Hybrid work
- New commerce opportunities in the Microsoft Store
- A low IT learning curve for deployment and management
- Beefed up security across devices and the cloud
- New tools and an easier Windows 11 application process for developers
- Some Subtle Hybrid Work Features
Microsoft has been promoting the hybrid work scenario for over a year because it is a real trend that has changed how most of us will work in the future. Microsoft is positioning Windows 11 as being hybrid work-centric.
Microsoft is bringing back widgets which are a feed powered by a back-end Artificial Intelligence AI to be personalized as possible.
Windows 11 offers new commerce opportunities. Microsoft is looking to make the Microsoft Store attractive to a much broader audience than just customers looking for the latest games. Microsoft is promising a better search experience and adding more business-oriented apps to the store
Microsoft wants Information Technology IT managers to be involved as little as possible in its push to Windows 11.
Windows 11 will be a zero-trust platform and this approach will span the entire Operating System landscape. That will include features like hardware-based isolation, encryption, and malware prevention all being turned on by default.
Can Windows 11 meet banks cybersecurity challenges?
In this section we assess windows 11 cybersecurity features with references to key issues raised at the Union of Arab Banks First Arab Banking Forum for Cybersecurity held in 7-9th October 2021 in Sharm el Sheikh, Egypt. The event addressed all cybersecurity issues surrounding banks, the Middle East and Arab countries who are are experiencing daily different kind of threats, such as distributed denial of service, spear phishing attacks, Credit Card Fraud, and others. The gap between motivated threat actors and security professionals has significantly grown and the traditional security solutions and controls are no longer sufficient to effectively protect the business.
The event gathered experts from the region to share their expertise, know-how and to recommend adequate solution for the changing threat landscape, raise awareness and deepen the knowledge of cyber security staff members in Arab banks and financial institutions about the modern technologies used by hackers and the new recommended solutions to mitigate the risks. Main topics were discussed including:
- Cyber Security Regulation – Enhancing banks cyber security posture
- Card Fraud Risk Management – Trends & techniques
- Minimizing incident impact through Zero trust architecture
- Incident Response Readiness – What you need to know & prepare
- SOC and Shift to Proactive Intelligence Response
- Threat Intelligence & Monitoring – Collaboration & Oversight
- Third party security risk management – Finding a partner you can trust
- Cyber Threats
- Today’s Cyber Attacks: Evolution of the Threat Landscape and Forecasts
- Malware Extended Detection and Response
- Accelerating your Zero Trust Journey
- Digital Transformation and API threats and Controls
- Dark Web Threat Hunting
- Cyber Security according to international security standards and framework.
With the above list of key cybersecurity topics in mind, it is obvious that Windows 11 can partially meet banks and financial institutions cybersecurity concerns. A robust cybersecurity program and strategy should be devised in order to leverage Windows Cybersecurity features. Banks and financial institutions need to buy new PCs for Windows 11. A considerable budget has to be set for the transition.
RECOMMENDATIONS FOR SOUND cybersecurity PROGRAM AND STRATEGY
Cybersecurity in digital banking is something that cannot be compromised with. With the growth in the digitalization in the banking industry, it has become more prone to attacks from cybercriminals. The banking sector ongoing digital transformation has caused potential cybersecurity attacks to grow, exposing organizations to increased levels of cyber threats. As more businesses adopt digital banking solutions, having an effective cybersecurity program and strategy is becoming increasingly important.
A key component to the success of cybersecurity programs is having an understanding of which threat trends pose the greatest risk to banks and financial institutions. Understanding the latest threat trends will help in building more informed security strategies that accurately assess the organization’s cyberhealth. By adopting programs that effectively monitor the security exposure, banking institution will be able to embrace digital transformation without compromising security or compliance.
Below are recommendations for sound cybersecurity strategy and program in banks and financial institutions:
- Developing a data protection strategy: Due to the high value of financial data, cybercriminals are increasingly targeting customer banking credentials when carrying out attacks. As more banks implement mobile banking applications, new vulnerabilities for cybercriminals to target are introduced to the network. Banking apps can be exploited from the client-side or the server-side, making them difficult to secure. This means that banks must be able to ensure that sensitive data is secure when it is being accessed from a customer device as well as when it is stored on bank servers.
- Control of operation with third party vendors: Cybercriminals attempt to target bank’s third-party vendors. Vendors have access to critical banking data but often lack stringent security policies, making them a prime target for threat actors. As banks increase their reliance on third-parties, it is important to continuously monitor cybersecurity. Proper vendor due diligence can save financial organizations from reputational damage and financial loss.
- Establishing security protocols: These protocols should comply with extant cybersecurity regulatory framework and protect systems, devices, and applications.
- Adopting Multi-factor authentication: Multi-factor authentication (MFA) is an authentication method in which access is only granted once a user presents two or more login credentials. Login credentials can include passwords, pins, or fingerprints.
- Undertaking regular cyber risk assessment: Performing a cyber risk assessment helps organizations identify and manage vulnerabilities within their network environment
- Having cyber insurance: Cyber insurance helps ensure that businesses are financially protected in the event of a data breach, making it an important component of a cybersecurity strategy.
- Employee training: For security programs to be effective, it is essential to train employees on cybersecurity best practices. Employee training can also help to minimize the impact of a data breach. When employees are trained to use cybersecurity systems properly, they can actively identify exploitable vulnerabilities in systems and make sure they are addressed.
REFERENCES
Windows 11 Security Guide and Book: Powerful security from chip to cloud, securityscorecard blog, sqn banking systems, enterslice, consultancy middle east, The Union of Arab Banks First Arab Banking Forum For Cybersecurity, KPMG Saudi Arabia.